Horizon Project
| Contents | Previous | 4.3 Action Mapping to Reduce Donors Affected by Leaks to Less than 1,000/Year | Next |
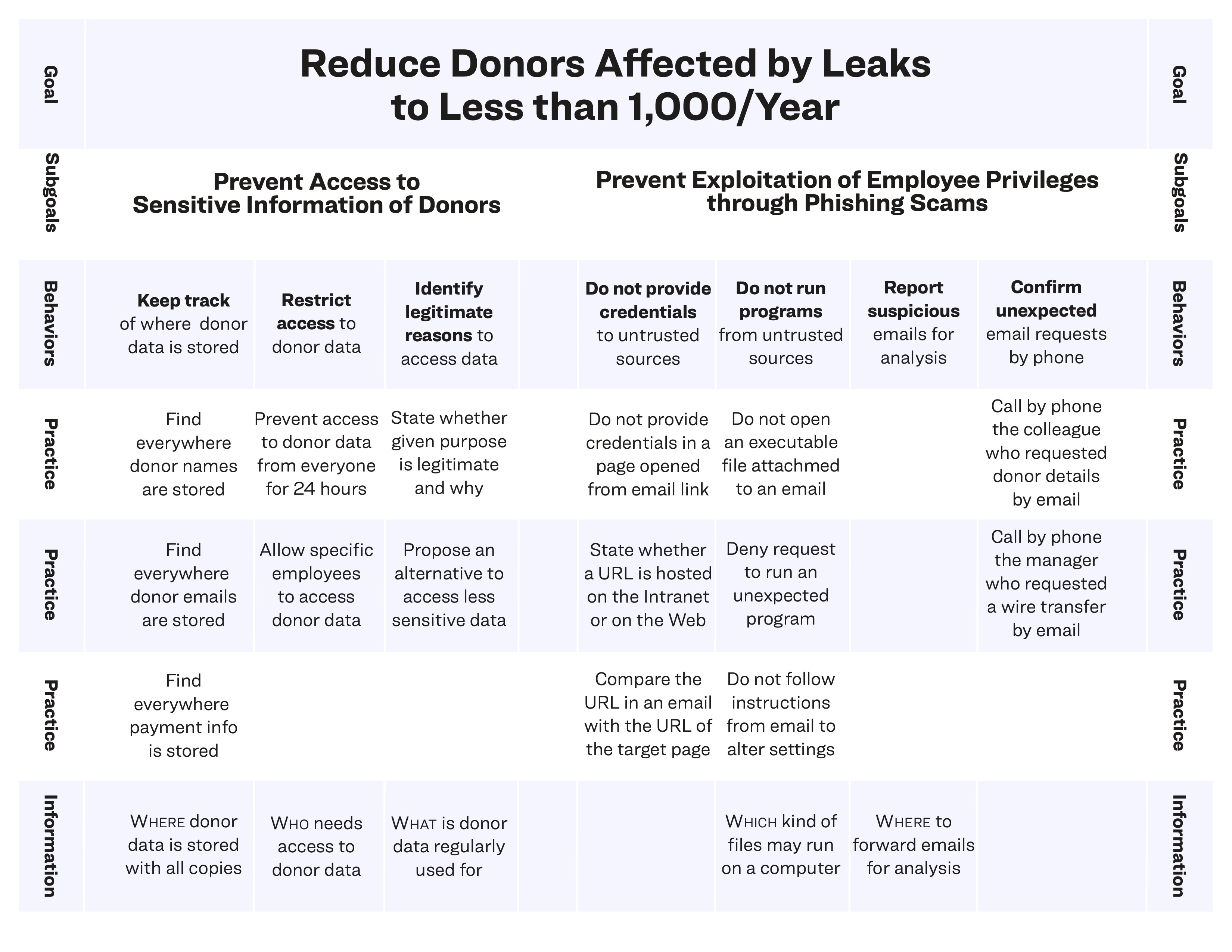
4.3 Action Mapping to Reduce Donors Affected by Leaks to Less than 1,000/Year
Subgoal: Prevent Access to Sensitive Information of Donors
Behavior: Keep track of where sensitive donor information is stored
Practice
- Find all files and databases where donor names are stored
- Find all files and databases where donor emails are stored
- Find all files and databases where donor phone numbers are stored
- Find all files and databases where donor addresses are stored
- Find all files and databases where credit card details of donors are stored
- Find all files and databases where bank details of donors are stored
- Find all files and databases where donation history of donors is stored.
Minimum Information
- Where donor information is first stored when they provide it
- Who has access to donor information, and for what purpose
- Where donor information is stored for subsequent usage.
Behavior: Restrict access to sensitive donor information
Practice
- Prevent access to sensitive donor information from everyone for 24 hours
Minimum Information
- All the files and databases where donor information is stored
- Who needs access to donor information, when, and for what purpose
- How to prevent and authorize access to files and databases.
Behavior: Differentiate legitimate reasons to access sensitive information
Practice
Given a purpose, state orally whether this is a legitimate reason and why. If the reason is not deemed legitimate, propose an alternative which does not require access to sensitive donor information.
Minimum Information
- Criteria to evaluate legitimate reasons to access sensitive information
- List of alternatives, using anonymous or aggregate information.
Subgoal: Prevent Exploitation of Employee Privileges Through Phishing
Behavior: Do not provide credentials to untrusted sources
Practice
Given an email received among other emails during a typical working day, with a link to a login page which requests user credentials, but is not stored on Horizon Intranet, the employee shall not input their credentials in the page.
Minimum Information
- How to recognize that a Web page is stored on the Intranet
- Dangers of phishing.
Behavior: Do not run programs sent by untrusted sources
Practice
Given an email received among other emails during a typical working day, with a link to download an executable file and instructions on how to run it on the computer, the employee shall not run the executable.
Minimum Information
- What is an executable file
- How to answer prompts to allow an executable file to run in a way that prevents the executable from running.
Behavior: Report suspicious emails
Practice
Given an email received among other emails during a typical working day, with telltale signs of an urgent or disproportionate request made by an unknown contact or by a known contact in an unusual way, the employee shall forward the email to the IT department for analysis.
Minimum Information
- Email of the IT deparment used to report suspicious emails
- Identify the claimed email address of the sender
- Awareness that the sender address can be spoofed
- Awareness that email of trusted contacts can be compromised (e.g. by a virus) to send emails pretending to originate from them
- Signs of a different voice (typography, syntax, level of language) used by a trusted source in a written email
- Signs of disproportionate requests or urgency
Behavior: Confirm unexpected requests received by email through a different channel
Practice
Given an email received among other emails during a typical working day, received from a trusted colleague, with an unusual request to provide sensitive information or financial details of donors, the employee shall call the colleague to confirm the request before complying.
Minimum Information
- Identify requests that lead to disclose sensitive information about donors
- Identify requests that lead to disclose financial details of donors
| Contents | Previous | 4.3 Action Mapping to Reduce Donors Affected by Leaks to Less than 1,000/Year | Next |